How To Crack Wifi Wpa2 Password Using Windows 10
1) Does This method actually work?? Ans: Yes, it works, but not on all kinds of networks and routers. As i mentioned in the above article using jumpstart you can hack only wifi routers secured with wpa/wpa2 - wps enabled 2) Jumpstart it shows Wireless configuration failed!what could be the reason for it not to be successful?
Accu chek aviva combo meter. > > > I do know a bit bout computers but for me to try that would be taking the > piss a bit!lol > > Thanks a lot Sid, I owe ya one, > Surfin' > > Regards, Sid. At the same time I had them send me some free batteries and control solution for my two active meters. I've just bought the software an IR adaptor and I'm very pleased with it. Mwillia at mweb dot co dot za Chris 02.03.03 13:42.
It’s the only really effective way to restrict access to your home Wi-Fi network. To potentially crack a password. For Windows 10? How To Hack Wifi Password In Windows ( WPS,WPA2,WPA ) – Latest Wifi Hacking Tricks Hack wifi Password in windows Hello tekgyd readers today i am.
Wpa2 Password Mac
Ans: Same answer as above, because it is not programmed to hack advanced routers. To put it into simple words, router is much more stronger than the attack 3) Hacking With JumpStart Failed, how should i hack this particular network now??
4) Networks Found in Wifi Tab but nothing in WPS Tab, what should i do not? Ans: This is neither your fault or Dumpper's or the system's fault. This happened because there are no WPS enabled networks near you, that's it.
It clearly means Dumpper can not hack the networks that are not WPS Disabled. So you need to go for another method of wifi hacking, which means you need to work a little on Kali Linux to hack, even though its not as easy as Dumpper. In case Jumpstart Failed to hack the router try the following (Hacking With Linux).
There are two types of ways to potentially crack a password, generally referred to as offline and online. In an offline attack, an attacker has a file with data they can attempt to crack. For example, if an attacker managed to access and download a password database full of hashed passwords, they could then attempt to crack those passwords. They can guess millions of times per second, and they’re only really limited by how fast their computing hardware is.
Clearly, with access to a password database offline, an attacker can attempt to crack a password much more easily. They do this via “” — literally attempting to guess many different possibilities and hoping one will match. An online attack is much more difficult and takes much, much longer. For example, imagine an attacker were trying to gain access to your Gmail account. They could guess a few passwords and then Gmail would block them from trying any more passwords for a while. Because they don’t have access to the raw data they can attempt to match passwords against, they’re limited dramatically.
(Apple’s in this way, and that helped lead to the huge theft of nude celebrity photos.) We tend to think of Wi-Fi as being only vulnerable to the online attack. An attacker will have to guess a password and attempt to log into the WI-Fi network with it, so they certainly can’t guess millions of times per second.
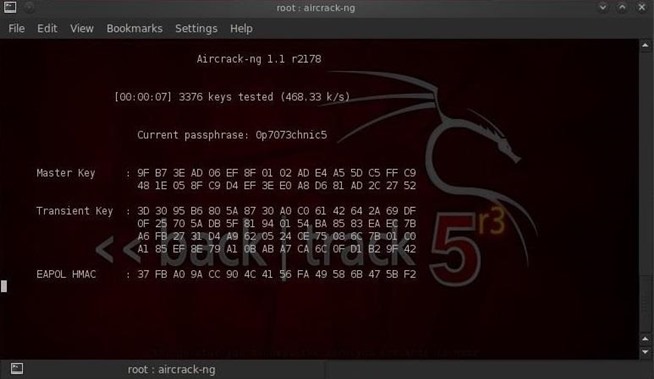
Unfortunately, this isn’t actually true. The Four-Way Handshake Can Be Captured. When a device connects to a WPA-PSK Wi-Fi network, something known as the “four-way handshake” is performed. Essentially, this is the negotiation where the Wi-Fi base station and a device set up their connection with each other, exchanging the passphrase and encryption information. This handshake is WPA2-PSK’s Achilles’ heel. An attacker can use a tool like airodump-ng to monitor traffic being transmitted over the air and capture this four-way handshake.
They’d then have the raw data they need to perform an offline attack, guessing possible passphrases and trying them against the four-way-handshake data until they find one that matches. If an attacker waits long enough, they’ll be able to capture this four-way handshake data when a device connects. However, they can also perform a “deauth” attack, which we covered when we looked. The deauth attack forcibly disconnects your device from its Wi-FI network, and your device immediately reconnects, performing the four-way handshake which the attacker can capture.
Image Credit: Cracking the WPA Handshake With the raw data captured, an attacker can use a tool like cowpatty or aircrack-ng along with a “dictionary file” that contains a list of many possible passwords. These files are generally used to speed up the cracking process. The command tries each possible passphrase against the WPA handshake data until it finds one that fits. As this is an offline attack, it can be performed much more quickly than an online attack. An attacker wouldn’t have to be in the same physical area as the network while attempting to crack the passphrase. The attacker could potentially use Amazon S3 or another cloud computing service or data center, throwing hardware at the cracking process and speeding it up dramatically.
As usual, all these tools are available in (formerly BackTrack Linux), a Linux distribution designed for penetration testing. They can be seen in action there. It’s tough to say how long it would take to crack a password in this way. For, it could take years, possibly even hundreds of years or longer. If the password is “password”, it would probably take less than a single second. As hardware improves, this process will speed up. It’s clearly a good idea to use a longer password for this reason — 20 characters would take a lot longer to crack than 8.
Find My Wpa2 Password Mac
Changing the password every six months or every year could also help, but only if you suspect someone is actually spending months of computer power to crack your passphrase. You’re probably not that special, of course! Breaking WPS With Reaver. There’s also an attack against WPS, an unbelievably vulnerable system that many routers ship with enabled by default. On some routers, disabling WPS in the interface doesn’t do anything — it stays enabled for attackers to exploit! Essentially, WPS forces devices to use an 8-digit numerical PIN system that bypasses the passphrase. This PIN is always checked in groups of two 4-digit codes, and the connecting device is informed whether the four-digit section is correct.
In other words, an attacker just has to guess the first four digits and then they can guess the second four digits separately. This is a fairly quick attack that can take place over the air. If a device with WPS didn’t work in this extremely insecure way, it would be violating the WPS specification. WPA2-PSK likely has other security vulnerabilities we haven’t discovered yet, too. So, why do we keep saying?
Well, because it still is. Enabling WPA2, disabling the older WEP and WPA1 security, and setting a reasonably long and strong WPA2 password is the best thing you can do to really protect yourself.
Yes, your password can probably be cracked with some amount of effort and computing power. Your front door could be cracked with some amount of effort and physical force, too. But, assuming you use a decent password, your Wi-Fi network will probably be okay. And, if you use a half-decent lock on your front door, you’ll probably be okay as well.